ASGER
Secure Access to Privileged Systems
Why Do We Need ASGER Platform?
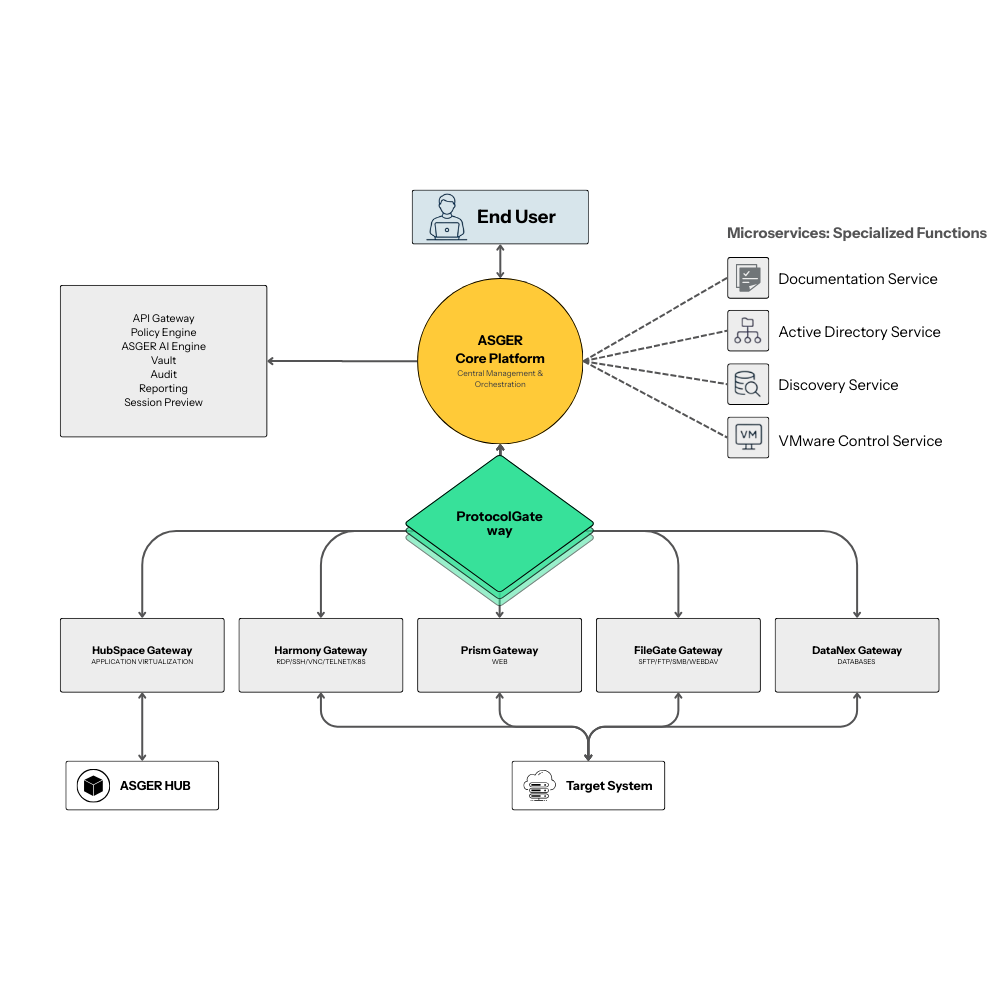
ASGER is a unified privileged access security platform built on a Zero Trust architecture, designed to centrally govern and protect access to enterprise-critical and operational infrastructure. It consolidates all privileged interaction points into a single, intelligent control plane—eliminating siloed access tools and reducing the attack surface across IT and OT environments.
ASGER seamlessly integrates core operational capabilities such as secure remote access (RDP, SSH, VNC, Telnet), database access management (DataNex), secure file transfer (FileGate), browser isolation (Prism), and container orchestration (HubSpace, Kubernetes). With multi-layer protocol awareness and policy-driven controls, ASGER ensures consistent security enforcement across diverse systems and workflows.
All privileged activities are continuously monitored and captured through Session Recording, providing full visibility and forensic-level traceability. The ASGER AI Engine applies machine-learning-based behavioral analytics to detect anomalies in real time, enabling proactive threat detection and actionable intelligence before risks escalate.
Integrated Vault services eliminate static credentials through automated rotation and Just-In-Time (JIT) access, significantly reducing credential exposure. Fine-grained policy orchestration enforces the principle of least privilege, ensuring users and systems receive only the access they need—only when they need it.
With built-in audit trails, compliance-ready reporting, and alignment with industry standards such as SOC 2, ISO 27001, and PCI-DSS, ASGER empowers organizations to meet regulatory requirements while strengthening their overall security posture—without sacrificing operational efficiency.
Cybersecurity issues according to 2019 Verizon DBIR report
Cyber Hygiene Compatibility
Protocol Support
Manages FTP, SFTP, SMB/CIFS, and WebDAV protocols from a single platform.
Advanced Security Rules
Maximum upload/download size limits can be defined, and operations are automatically blocked in case of policy violations. File extension and MIME type–based allow/deny lists ensure that only permitted file types can be transferred. Performs file analysis with malware scanning and Sandbox integration.
Granular Control
Individually controls upload, download, delete, rename, mkdir, copy, and move operations.
Remote Browser Isolation (RBI)
Full Control Mode / Restricted Mode
The user has full control over the remote browser and experiences a native browser experience.
Multi-Browser Support
Web Automation
Form filling, data collection, and repetitive tasks are automated within a secure containerized environment.
Virtual Firewall / DNS Filtering
Database Clients & VS Code
Runs database management and development tools such as Visual Studio Code and DBeaver. Provides a secure environment for external project developers.
Broad Database Support
Command Blocking
Data Masking
Switch Database Control
Controls users’ database switching permissions (e.g. USE database, c database). Prevents lateral movement and ensures data isolation.
BENEFITS & FEATURES
- Anomaly Detection
- Agent Free Structure
- OCR Processing
- Fully Session Record
- Multi Factor Authentication
- Dynamic Display Quality
ASGER components are located in distributed roles on the same server or different servers with its unique security architecture.
-
Fast switching between active sessions and keyboard broadcasting feature
Multiple sessions can be opened simultaneously and the same keyboard data can be entered simultaneously..
-
High-level security with offline two-factor authentication.
-
More secure access to web applications with hub technology.
-
Anomaly detection and enhanced risk visibility
Secure access solution to RDP, SSH, Telnet, VNC, Web and Kubernetes services
Encrypted and Secure Vault
It secures the accounts used in RDP, SSH, VNC, TELNET and KUBERNETES connections.
Frontend Security Layer
It reduces security risks by creating a front layer of security for suspicious activities which target critical systems and malicious actions by attack actors.
Enhanced Video Recording
It helps to track access logs in cases of compliance violations and gather information on broad access-related activities.
Container (Docker) Technology
It ensures rapid growth and uninterrupted operation of systems.
WorkHub Technology (WEB APP)
Equipped with Selenium module, ASGER WORKHUB technology provides secure access by recording the user-specific flexible experience and session without the need to install an additional server while the user is accessing web-based applications.
Real-time Multiple Sessions and Automatic Video and Typescript Recording of Sessions
the most practical pam solution
the most practical pam solution
In the Management Interface
- Account and account group identity management
- Management of account and account group roles
- Account access policy management
- Account and account group authorization
- Account preferences
- Application and application group management
- App usage statistics
- Share profile management
- Using quick access (AppConnect)
- With reporting and statisticsr
With Customized Interface
- Display performance options
- Visibility related options
- Entering the total number of connections and the total number of connections per user
- Instant application access limits
- Ability to define application sharing profile as “Read-only”
- Language change option
- Mobile-specific mouse cursor or touchscreen management option
- Password change possibility
With all applications, application groups and sharing profiles defined on the system;
- It provides secure access by recording both video and sessions on remote systems by using the selected application protocol without any application and authorization definitions.
- The feature about providing session access to even anonymous people with the links given within the required permissions.
- Automatic authentication to the user with SSO data transmission.